Monitor endpoint ransomware preparedness
Ransomware is one of the most significant threats to businesses worldwide. Increase your organization’s ransomware preparedness and assure that the tools needed for remediation, eradication, and recovery are always in place and functioning as expected.
Highlights





Assess your strategic ransomware readiness
Establish a cyber hygiene baseline across endpoints
- Absolute cybersecurity experts evaluate your existing security posture across your Absolute endpoints to identify key security controls (e.g., anti-virus/anti-malware, endpoint protection, or endpoint detection and response solutions), as well as device management tools that are required to minimize ransomware exposure and assure expedited recovery efforts.
- Jointly, we establish policies that automate monitoring and self-healing of essential device management tools and security controls that are needed to detect, restore, and prevent ransomware. In addition, we train your personnel on how to monitor application health and apply these baseline policies to new devices as they are enrolled.

Provide remote assistance in your endpoint recovery efforts
Expedite recovery tasks
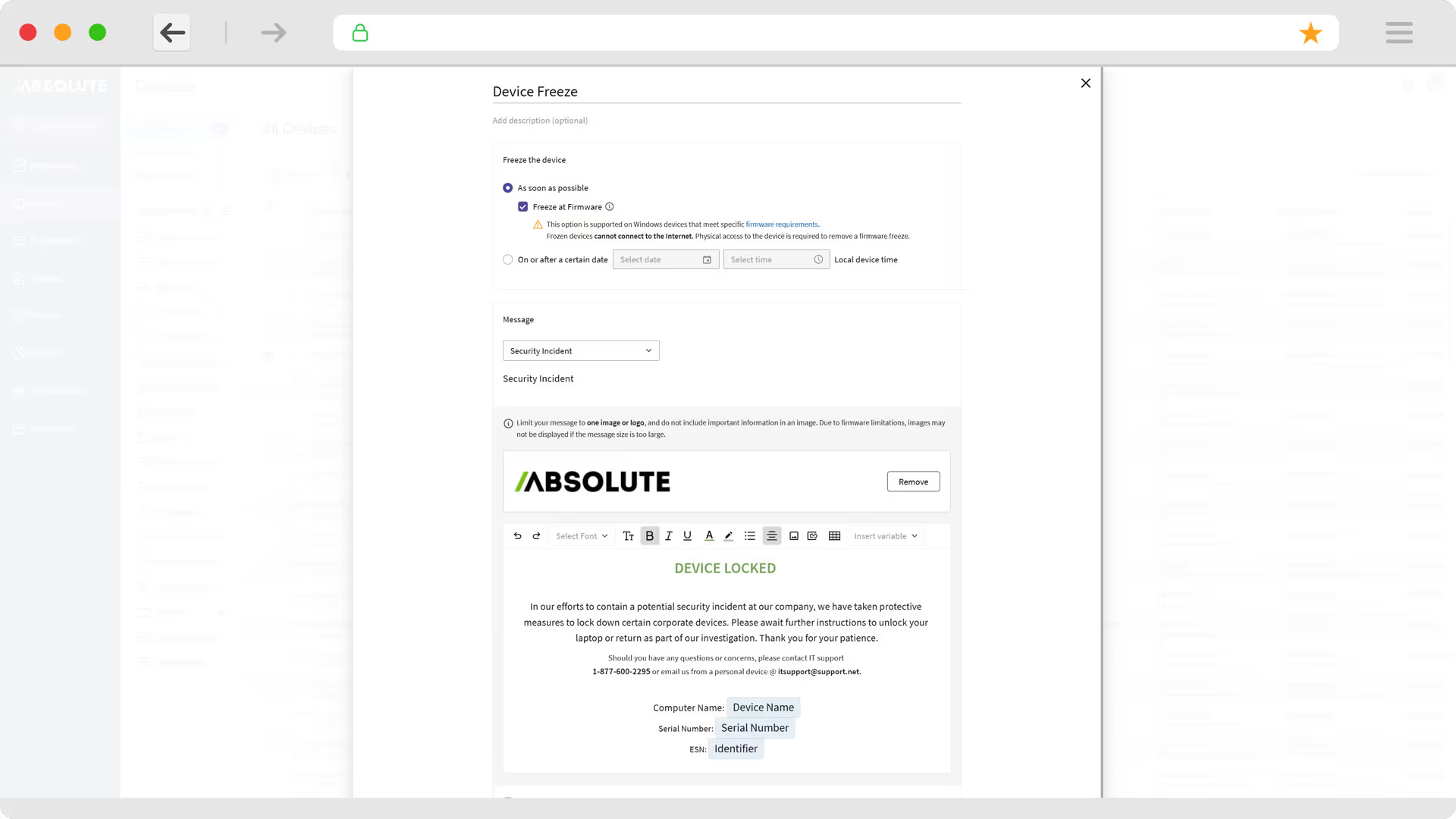
- We equip you with the capabilities to communicate with end users even when their devices are compromised, and to freeze endpoints to preserve evidence for litigation purposes while limiting further spread of infection.
- Ensure that endpoint security and device management tools that might have been rendered inoperable are functioning, even under distress, and execute workflow and task automation commands to expedite device recovery, leveraging a library of custom scripts.

Featured resources
Absolute Ransomware Response FAQ
Absolute Ransomware Response enables customers to assess their ransomware preparedness for endpoints, monitors their endpoint cyber hygiene across the device fleet, and allows for an expedited endpoint recovery leveraging Absolute’s always-on connectivity, automated restoration capabilities for key security and management tools (e.g., Microsoft® Endpoint Manager, Ivanti®, Tanium™, SentinelOne®, CrowdStrike™), and library of Absolute Reach scripts.
Absolute Ransomware Response addresses the following negative consequences when it comes to falling victim to a ransomware attack and facing delays in recovery efforts for endpoints:
- Prolonged shutdown of company’s business operations, specifically user recovery and endpoint restoration.
- Lower employee productivity due to lengthy recovery efforts for remote devices.
- Increased support costs from higher volume of help desk tickets by panicked end users when encountering ransom notices on their devices.
- Financial loss associated with complex remediation efforts.
- Risk of burn out and high attrition due to the demands being put on hard-pressed IT admin and security teams when it comes to recovery efforts for endpoints.
- Reputational damages due to extended outages.
The Absolute Ransomware Response product delivers the following capabilities:
- Check Strategic Ransomware Readiness Across Endpoints
- Enable Ransomware Cyber Hygiene Across Endpoints
- Report on Hardware and Software Inventory
- Assess Device Security Posture
- Discover Sensitive Endpoint Data
- Secure, On-Device End User Communications
- Freeze At-Risk Devices
- Expedite Recovery Tasks
- Self-Healing for Endpoint Security Tools
- Self-Healing for Device Management Tools
- Assist in Ransomware Recovery for Endpoints
At the beginning of the engagement, a professional services technical consultant will review the existing standard security controls across endpoints, identifying key controls (e.g., anti-virus/anti-malware, endpoint protection, or endpoint detection and response solutions) and device management tools that are required to minimize ransomware exposure and assure expedited recovery efforts.
At the beginning of the engagement, a professional services technical consultant will help establish application resilience policies to ensure that identified mission-critical security applications and device management tools are installed and functioning as intended. In addition, a professional services technical consultant will train customer personnel on how to continuously monitor application health and apply these baseline policies to new devices as they are enrolled.
A professional services technical consultant will remotely help in endpoint recovery efforts for up to two incidents per year, following a pre-defined playbook and leveraging the existing Absolute product capabilities.
Absolute Ransomware Response is available on Windows devices only since it is the most common OS-target for ransomware attacks.
Absolute Ransomware Response yields the following benefits:
- Check customer’s strategic ransomware readiness
- Establish a cyber hygiene baseline across endpoints
- Expedite recovery tasks
- Provide remote assistance in endpoint recovery efforts by sharing proven expertise, putting less demands on hard-pressed IT admin and security teams.
The Absolute Ransomware Response Add-On for Control customers delivers Ransomware Readiness Check, Ransomware Cyber Hygiene Enablement, Ransomware Recovery Assistance, Reach, Endpoint Data Discovery, as well as Self-Healing for one management application (e.g., Microsoft SCCM, Microsoft Intune) and one anti-malware application.
The Absolute Ransomware Response Add-On for Resilience customers delivers Ransomware Readiness Check, Ransomware Cyber Hygiene Enablement, and Ransomware Recovery Assistance.