Absolute Control
Retain command of all your endpoints, all the time – even if they’re off your corporate network

Take action to safeguard your devices, applications, and data
Endpoint visibility is important. However, it’s even more crucial to safeguard your devices, applications, and data based on what you’ve learned by gathering the truth across your endpoints. Endpoint control is the next step in your endpoint management and security strategy.

Highlights
Absolute Control™ includes all the capabilities of Visibility™ plus critical endpoint control functions:

Define geofences to detect unauthorized device movement and be alerted when a device crosses an established boundary.

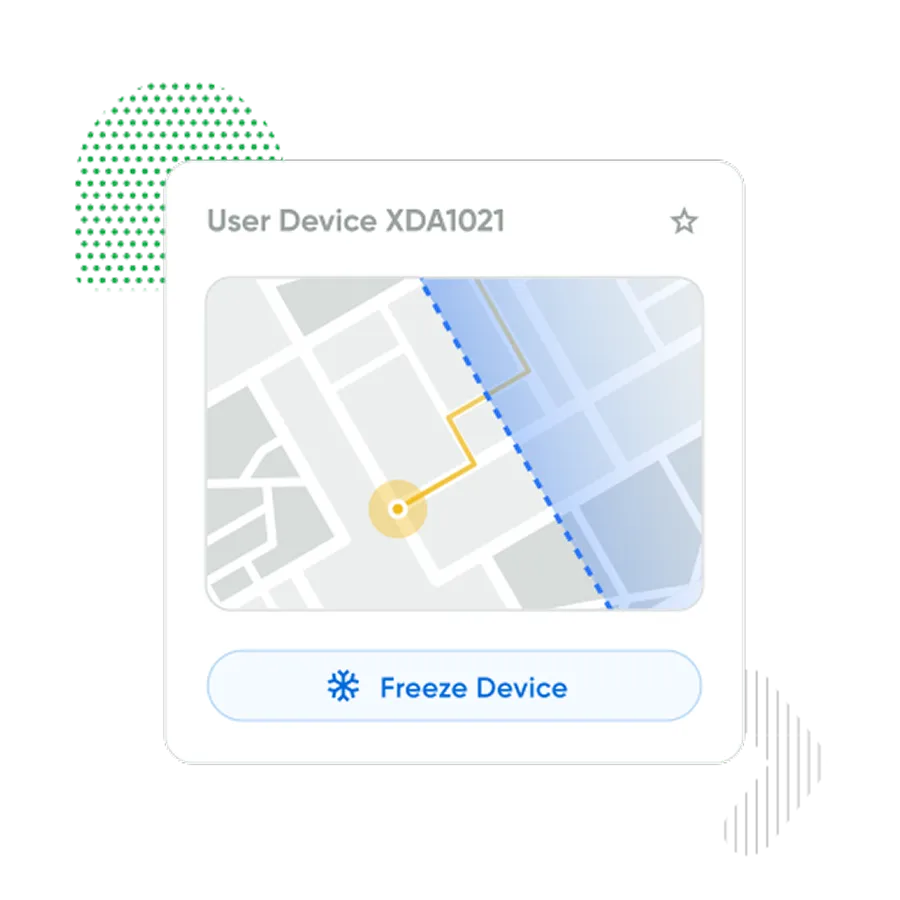
Freeze devices when threats have been detected, and notify users with a custom message - automated or on demand.

Selectively delete files on any device from anywhere and remotely perform an end-of-life device wipe in accordance with NIST 800-88 with compliance certificate.

Inform users in a coordinated fashion by displaying important messaging in real-time on their devices’ screen or to solicit feedback even if their device has been compromised or other communication tools have been rendered inoperable.

Improve missing device return rates by leveraging capabilities like on-device end user communications, device freeze, and geolocation tracking.

Create, remove, or change supervisor password remotely and at scale on specific Lenovo devices.

Configure custom visualizations to track current compliance status and historical trends related to devices and applications.

Obtain tailored endpoint, security and compliance information across your environment by asking questions to the Absolute AI Assistant.
Safeguard your devices
Earn trust and prove compliance
- Freeze lost or stolen devices. Set geofences and timers to automatically trigger these actions whenever a device leaves a safe area or stops calling in.
- Selectively wipe data from at-risk endpoints. Perform end-of-life device wipes remotely and generate compliance certificates.
Send secure, on-device end user communications
Reach your end users whenever needed
- Display important messaging on your users’ devices, preventing unnecessary help desk support calls and fragmented communications. Avoid confusion when informing users of an upcoming IT event, providing instructions on how to avoid any imminent ransomware threats, or soliciting feedback through surveys.
- Enable continuous, real-time communication even when other communications tools are offline or have explicitly been rendered inoperable by malware or ransomware.

Enable firmware protection without bringing devices in
Remotely manage supervisor passwords
- Get unprecedented control over your endpoint security configurations — and prevent unauthorized changes to them — by remotely managing supervisor passwords for supported Lenovo devices.

Obtain device and security insights
Build custom dashboards for your unique requirements
- Configure widgets, dashboards and reports aligned with IT and security policies.
- Analyze current status and historical trends across attributes, including asset management, device risk, compliance, and app usage.
- Access granular insights on encryption status, device location, and web or software activity.
- Query for tailored device and security information across your environment using the Absolute AI Assistant.

What our customers love about Absolute Control

As a CIO, Absolute Secure Endpoint gives me peace of mind so I can sleep at night. It has strengthened our security posture, allowing us to stay in compliance and giving us that extra level of comfort.
Simple and flexible packages
Discover how Absolute keeps your devices secure, resilient, and always connected.
Explore Secure Endpoint products

Serves as your source of truth for device and application health.

Provides you a lifeline to protect at-risk devices and data.

Delivers application self-healing and confident risk response.

Provides seamless and proactive patch management.

Offers remediation of security vulnerabilities through automated workflows.

Boosts ransomware preparedness and time-to-recovery.
Explore Secure Access Products

Built from ground up for mobility and the modern edge.

Delivers the best user experience for the software-defined perimeter.

Comprehensive SSE provides security controls and threat protection across web, cloud, and private apps.

Boosts diagnostics and remediation for digital experience monitoring.

Web security that protects data, prevents threats, and secures access to cloud apps.
Related product packages
Specifically tailored capabilities for Chromebook users.
Specifically tailored capabilities for Windows student devices.
Specifically tailored capabilities for Education customers.
Featured resources
Secure Endpoint FAQ
Absolute Secure Endpoint is one of our company’s core product lines, which leverages the unbreakable connection provided by Absolute Persistence® to enable IT and security personnel to monitor and address computers' problems and enables the computers and their mission-critical applications to self-heal. This helps with IT management, strengthening a company’s security posture, and maintaining compliance.
The Absolute Secure Endpoint product portfolio contains a variety of product packages:
- Absolute Visibility
- Absolute Control
- Absolute Resilience
- Absolute Resilience for Security
- Absolute Resilience for Automation
- Absolute Ransomware Response
Other variants, such as Absolute Resilience for Student Devices, may be offered to meet particular use cases or geographic market needs.
Absolute Control is the mid-service tier in the Absolute Secure Endpoint portfolio. Absolute Control adds to Absolute Visibility’s capabilities to control endpoints over the Internet, allowing for critical functions such as remote file deletion and data wipe, freezing devices on demand when at-risk, end user messaging, as well as establishing geo-fences and alerts.
Absolute Resilience is the third product edition in the Absolute Secure Endpoint product portfolio. Compared to Absolute Control, it adds further capabilities to secure endpoints from IT or security risks, respond to unexpected downtime due to security breaches and incidents, and enable Application Resilience to automatically monitor and detect unhealthy applications and automatically heal them.
Absolute Resilience for Security is the fourth product edition in the Absolute Secure Endpoint product portfolio. It combines all the capabilities of Absolute Visibility™, Absolute Control™ and Absolute Resilience™ with the Patch module, enabling IT and security teams to scan their endpoint population to assess patch health in relation to known operating system and software vulnerabilities.
Absolute Ransomware Response is a stand-alone offering, which provides capabilities and services to assess an organization's ransomware preparedness and cyber hygiene across endpoints; ensures mission-critical security applications such as anti-malware and device management tools remain healthy and capable of self-healing; and expedites the quarantine and recovery of endpoints if a ransomware attack occurs.
Customers can easily upgrade/downgrade their product subscriptions between Absolute Visibility, Control, Resilience, Resilience for Security and Resilience for Automation. Capabilities are additive and enabled via a software license key.
Absolute Ransomware Response is offered as a stand-alone solution primarily for security-conscious customers. Add-on options are offered for Absolute Control, Resilience, Resilience for Security and Resilience for Automation customers.
Absolute can be purchased through leading device manufacturers, resellers, and distributors. Contact us and we would be happy to help you with this process.

















