ABSOLUTE SECURITY CYBER RESILIENCE PLATFORM
We Stop DowntimeSM
Resilient CISOs trust us to prevent and minimize business disruption and recover in minutes from cyber incidents.
Few organizations fully recover from an incident
"Cyber incidents are now a normal — even mundane — occurrence."
"As a result, CISOs must prepare for what senior leadership will want (resilience) over what they once wanted (protection)."
Source: Gartner Research, Maverick Research: CISOs Must Transform Their Role or Become Obsolete, Will Candrick, 19 June 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
annual cost of downtime
(Splunk + Oxford Economics, 2024)
average ransomware/extortion cost
(IBM/Ponemon, 2025)
average data breach cost
(IBM/Ponemon, 2024)
of supply chain breaches are from third-party vulnerabilities
(Verizon DBIR, 2024)
breach cost in shadow AI-heavy organizations
(IBM/Ponemon, 2025)
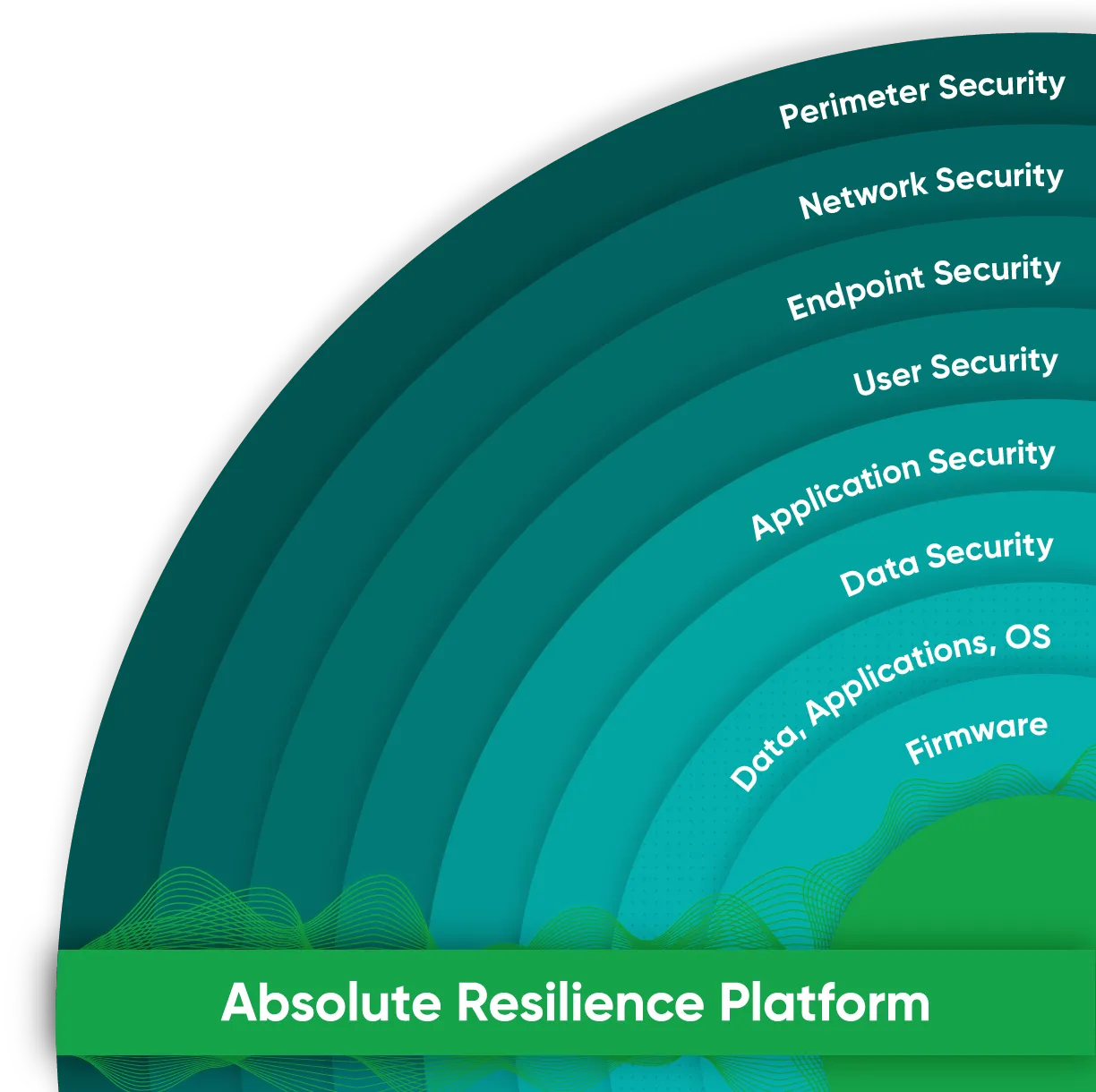
You need an enterprise platform that drives resiliency across your security stack
The industry's only firmware to cloud enterprise resilience platform
Operates un-deletable at the BIOS level, the only resilience platform you can't remove.
Remotely recovers devices in minutes to a trusted state—not days—without IT delays.
Self-heals before downtime or breaches spread, across endpoints and applications.
Automates patching and vulnerability remediation with 100% control and resilience, for endpoints and servers.
Delivers AI-powered, audit-ready security and compliance with 100% confidence, for CISOs.
30+ years of enterprise
cyber resilience
devices with
Absolute embedded
global
PC OEMs
daily API calls
from endpoints
patents
worldwide
monthly application
health scans

Stop downtime in minutes, not hours or days
The Absolute Security difference

Persistence
Only Absolute Security's patented persistence technology is embedded in the firmware of over 600 million devices.
Resilience
Only Absolute Security creates an unbreakable connection between device firmware and the Absolute platform.

Intelligence
Only Absolute Security's platform and data uniquely delivers cyber resilience across your entire security stack.
Resilient CISOs and CIOs
rely on us
“Resilience is so important to how you as a CIO or CISO ensure that your organization can weather a breach, ransom attack, or pandemic.”
“I can sleep at night because of Absolute Security. As a CIO, Absolute Secure Endpoint gives me peace of mind. It has strengthened our security posture, allowing us to stay in compliance and giving us that extra level of comfort.”
Recognition, validation,
and certifications

Recognized in Gartner® Hype Cycle™ for Zero-Trust Technology, 2025

Recognized in Gartner® Hype Cycle™ for Workspace Security, 2025

GigaOm Radar Report Leader, Patch Management Solutions, 2025

GigaOm Radar Report Outperformer, Patch Management Solutions, 2025

Recognized as a Leader in Frost Radar™ for Endpoint Security, 2025

FedRAMP authorization to operate (ATO)

Certified ISO/IEC 27001

Service Organization Control 2 (SOC2) compliant

Endpoint Management and Zero Trust Networking Leader, Enterprise, G2, Fall 2025

Zero Trust Networking, Enterprise, G2, Fall 2025
Trusted worldwide for
business continuity

of Fortune 500
enterprises

of the top 40 Fortune 500 healthcare providers

of the top 60
global banks








